This is an analysis of the lockpick 2.0 sherlock from Hack the Box. The provided binary is called update. Running file on the binary returns:
update: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), statically linked, no section header
Which is odd because usually it tells you a bit more information. When opening the file in binary ninja I can see the string UPX.
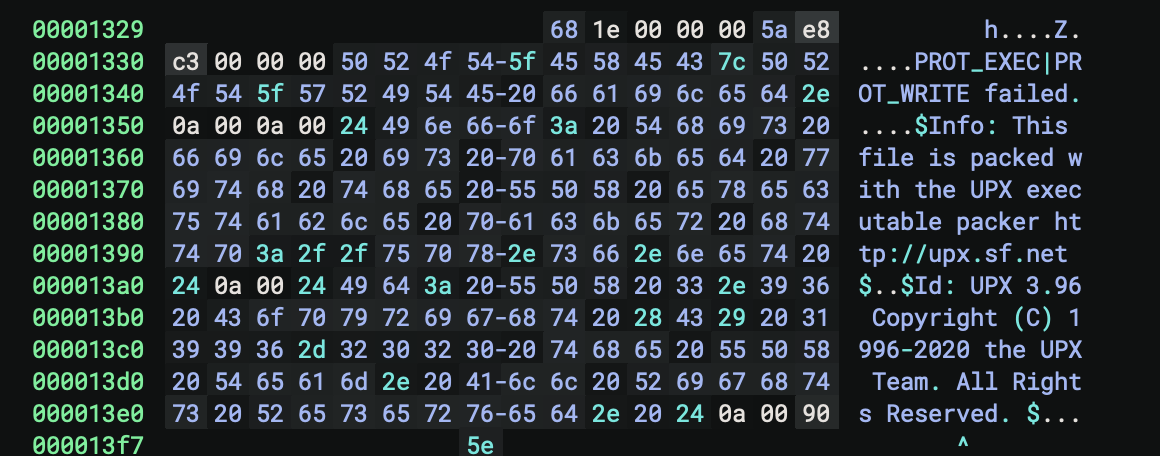
It also detects a few functions which also suggests that the sample is packed.
To unpack upx you can download the upx binary and run the following command.
upx -d updater
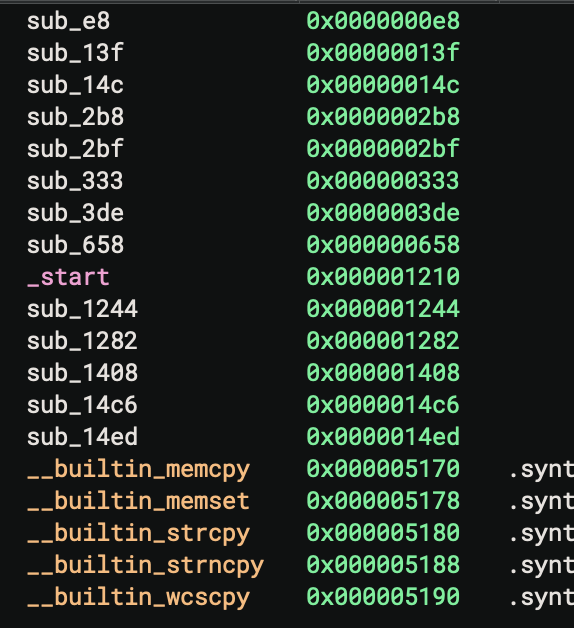
Now I have an unpacked version of the binary. Opening the binary again in binary ninja shows more functions!
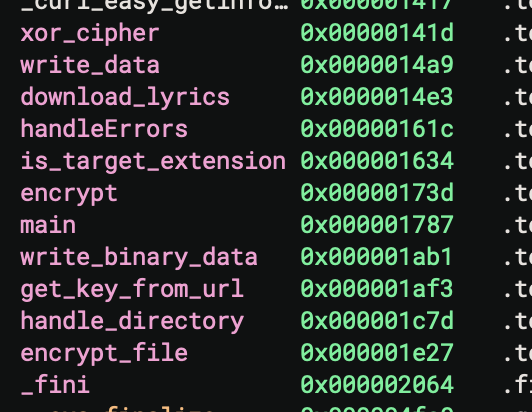
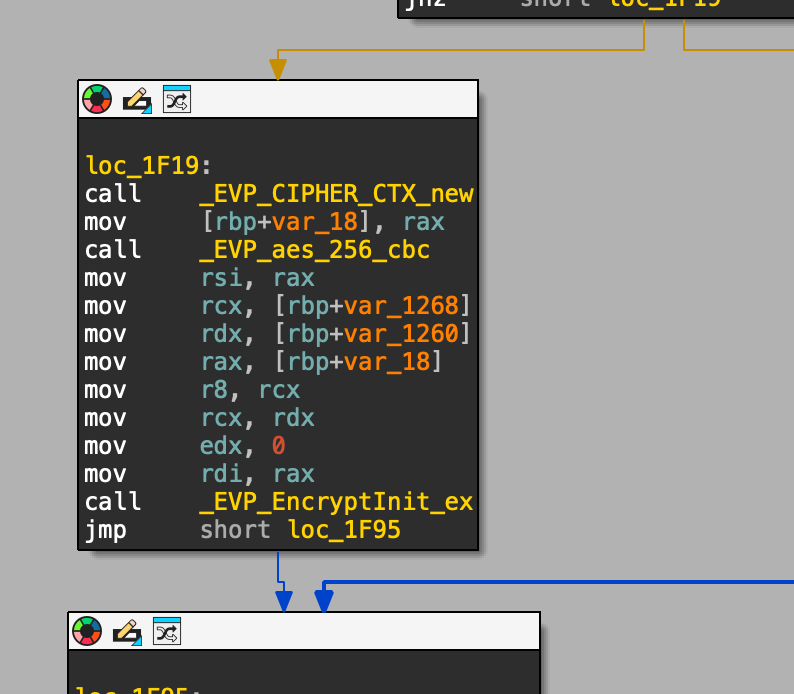
Examining the encrypt_file function it looks like they are using aes 256 cbc encryption.
Running the sample in gdb and breaking on the get_key_from_url gives me the url of the key used for encryption.
b get_key_from_url
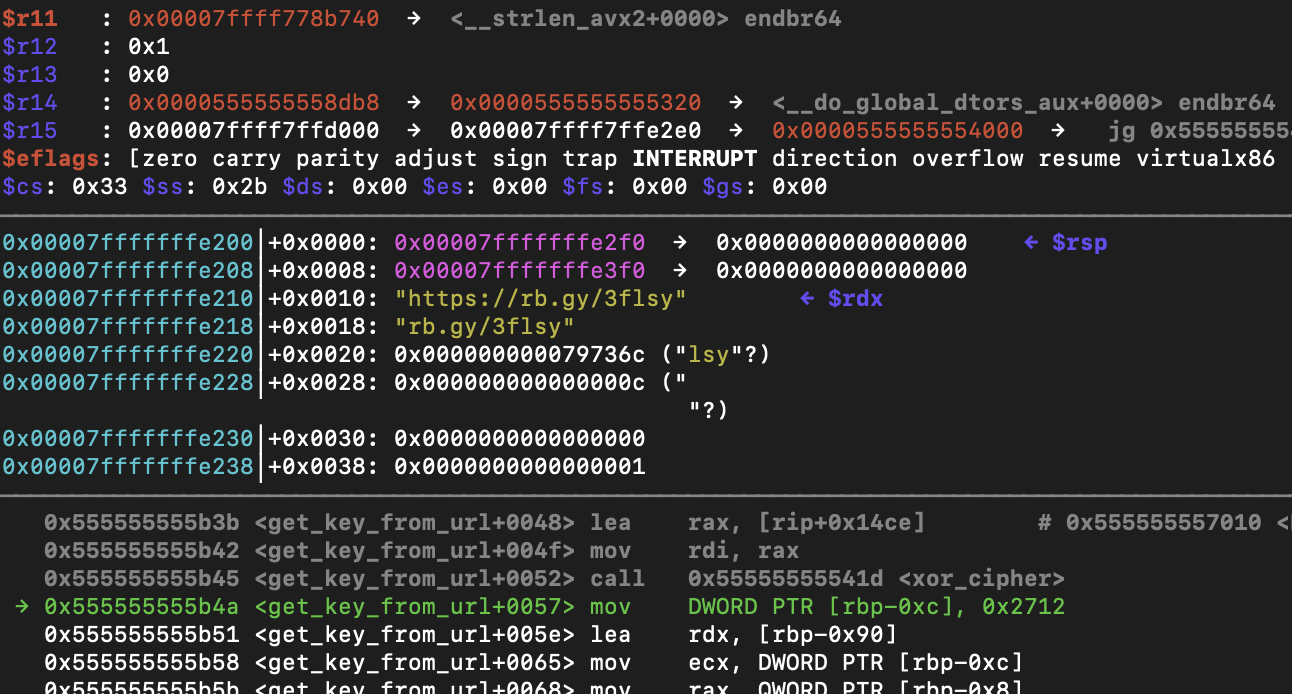
Finally we can decrypt the encrypted files using the key and iv from the downloaded file. The below screenshot shows how the first 32 bytes of the file are memcopied into a variable and the other half is used as an IV.
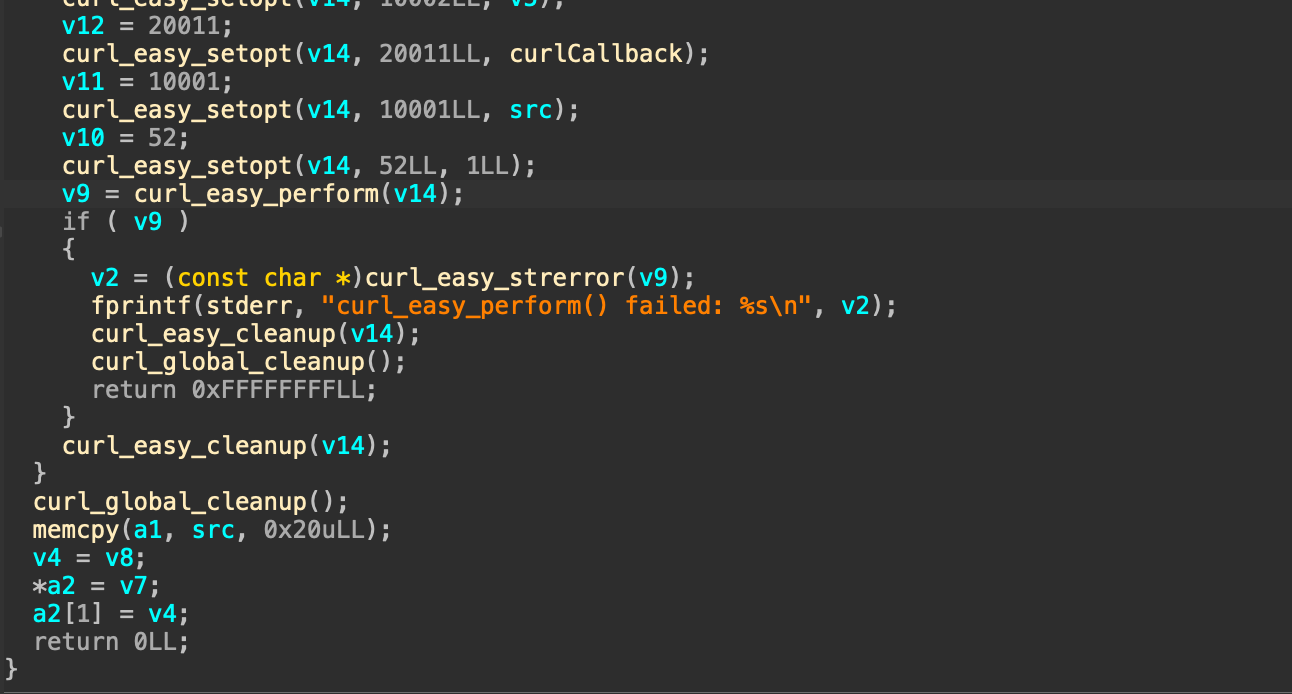
The following script decrypt the files.
1import os
2
3# AES 256 cbc
4
5from Crypto.Cipher import AES
6from Crypto.Random import get_random_bytes
7from Crypto.Util.Padding import pad, unpad
8
9
10def decrypt(ciphertext, key, iv):
11 cipher = AES.new(key, AES.MODE_CBC, iv)
12 decrypted_text = cipher.decrypt(ciphertext)
13 return decrypted_text
14
15key_material = open("updater","rb").read()
16
17key = key_material[0:32]
18iv = key_material[32:]
19
20for filename in os.listdir("."):
21 if "24bes" in filename:
22 print("decrypting", filename)
23 ciphertext = open(filename,"rb").read()
24 out = decrypt(ciphertext, key,iv)
25 open(filename[:-6],"wb").write(out)
Final Thoughts
If a sample is using unmodified upx it is straightforward to unpack. Once unpacked, the sample was a simple ransomeware malware that used the same key and IV for every file. The key and IV were downloaded from the domain found in the binary.